Latest news of interest from Janco's news feed
Disaster Recovery Planning, Job Descriptions, Salary Survey, Business Continuity, ITSM, SOA, Compliance, SOX, and HIPAA
The Janco News feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
If you wish to subscribe to this news feed the options that you have are:
AI buyers and users need to be aware of AI generative risks
Tools that the CIO, CSO, CTO, and CFO can use for Infrastructure, Disaster Recovery, Security, Job Descriptions, ITSM, Salary, Change Control, and Help Desk.
Risks increase as AI goes mainstream with the moves towards the Artificial Intelligence and Machine Learning
Companies and individuals are seeing real-world fallout from gen AI models choosing between doing the best answer for who is paying for it, the vendor producing it, the end user using it, or its own hallucinated goals.
In one case AI agent at coding startup deliberately violated instructions, deleted a production database, and tried to cover it up. another case xAI's Grok was searching online for Elon Musk's opinion before giving answers to certain questions.
It's not surprising that AI understands who created it. In fact, it would be difficult to train a model that didnt know who it worked for. The most difficult task is turn offing any access to the internet and remove any hint the AI was created by a particular company.
And why would an AI company bother? They are organizations with the intention of creating real value in the real world. A company that doesnt have a bias toward its own offerings wont exist for long.
Switching to open-source models is no panacea. The problems are related to compliance and is security,. If you go to a community model, theres no vetting. You dont know what youre getting.
And some of the most popular open-source models, such as China's DeepSeek, come with their own risks of potential bias that will keep many corporate users from adopting them.
Order Manager Artificial Intelligence Job Description
Texas enacts Telemarketing and Spam laws
Compliance Management Made Easy
Effective September 1, 2025, Texas Senate Bill 140 expanded Texas's telemarketing law (sometimes referred to as a "mini-TCPA") to cover text messages and images in addition to phone calls. This does not alter the existing consent and opt-in requirements.
Key elements:
- Solicitation Hours: Marketing calls and texts are only permitted between 9:00 a.m. and 9:00 p.m., Monday through Saturday, and between 12:00 p.m. and 9:00 p.m. on Sundays (recipient's local time).
- Identification: All solicitations must clearly identify the sender, the business, and the purpose of the call or text. See solicitation requirements.
- Registration: Businesses that send solicitations from Texas or to Texas residents may be required to register with the Texas Secretary of State and post a security deposit, unless an exemption applies.
- Enforcement: Violations may result in fines or lawsuits brought by the Texas Attorney General or consumers. Importantly, individuals now have the ability to bring lawsuits directly under Texas law.
Many other states have enacted similar "mini-TCPA" laws with their own guidelines on solicitation. Please note that this for awareness only and does not constitute legal advice or ongoing regulatory support.
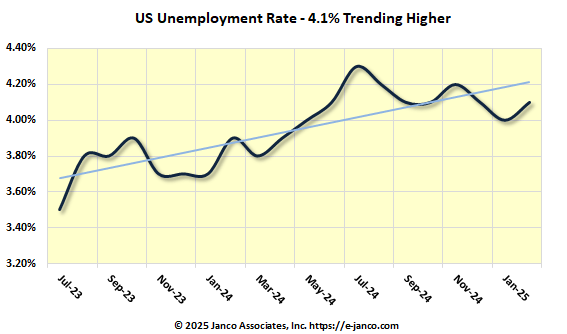
BLS Data is Suspect
Janco Reports BLS Sets IT Unemployment Rate at 5.5%
Janco reports that, according to the data provided by the BLS, the prospects for new jobs are worsening. We do this with one caveat about our concern for the quality of the BLS data. For example, the BLS adjusted down the number of jobs reported for May and June by 13,600 versus an initially reported gain of 1,400 jobs for the same period. Adjustments at those levels of magnitude are not acceptable from any organization. It can only be due to poor data capture, poor infrastructure, incompetence, or political gerrymandering.
Since the start of COVID, the BLS data presented on the first Friday of the month have had MASSIVE adjustments. This past month, the magnitude of the adjustments was at a 50-year high.
In response to this data, Trump has fired the head of the BLS. Only time will tell if these adjustments will continue.
White Papers Available for Download
White Papers
Janco has published serveral white papers which are available for download. They are:
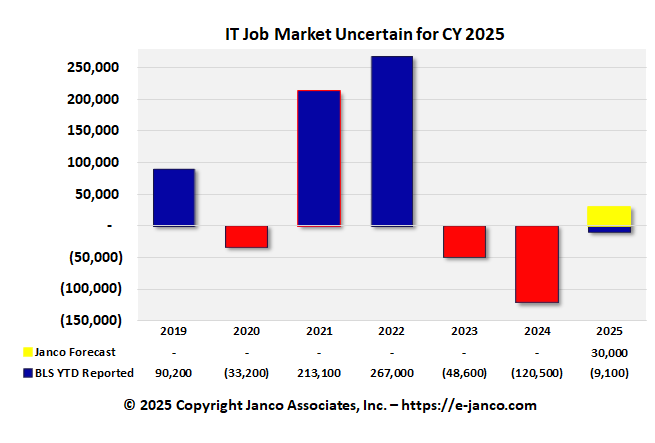
Employment Picture for IT Pros is Spotty
4.1 million individuals are employed as IT Pros in the US
With all of the talk about DOGE, tariffs, and the possibility of a recession in the 3rd or 4th quarter of this year, CIOs are slowly stopping the growth of their IT Staff and technology initiatives. The February employment numbers by state which the BLS released show that trend.
Job descriptions are now key tools which both employer and employee need to understate for roles and respinsibilities.
C-Level Director Level Managers Mid-Mgt Staff
IT Governance and Infrastructure Released
IT Governance and Infrstructure Released - 11 key job descriptions including Chief Artificial Intelligence Officer
The IT Governance Infrastructure, Strategy, and Charter Template addresses every critical governance and infrastructure issue, including: IT management structure; strategies and responsibilities; priority setting; personnel practices; ERP and Omni Commerce; compliance and
controls; and security/access controls.Information Technology and digital resources are changing the ways that enterprises operate, employees and enterprise associates interact on a day-to-day basis, and customers and suppliers access enterprise assets remotely. That, along with the exposures and risks that are placed on critical and sensitive information, places stress on the traditional governance models that are in place.
To support the process, the IT Governance offering includes eleven (11) full job descriptions:
- Chief Technology Officer (CTO)
- Chief Information Officer (CIO)
- Chief Information Officer (small enterprise)
- Chief Artificial Intelligence Officer (CAIO)
- Chief Compliance Officer (CCO)
- Chief Experience Officer (CXO)
- Chief Security Officer (CSO)
- Chief Data Officer
- Chief Digital Officer
- Chief Mobility Officer (CMO)
- Digital Brand Manager
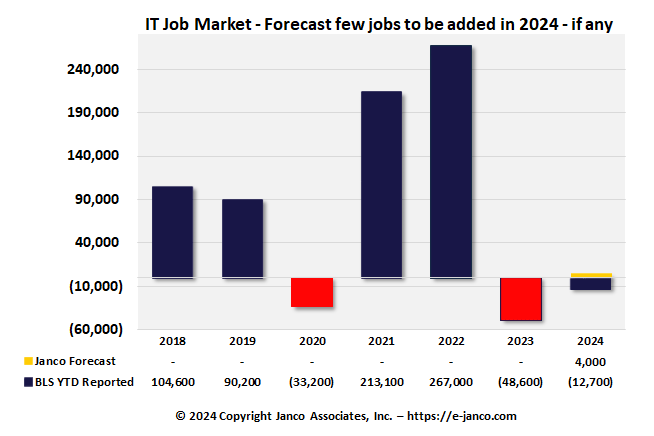
Hiring of IT Pros has has slowed - IT job market softens
Hiring of IT Pros has has slowed - IT job market softens
IT Job Market Soft - A pair of reports on tech sector employment trends in the United States suggest out-of-work techies have relatively decent prospects, but economic uncertainty and rapid policy changes initiated by the Trump administration mean the future job market looks less rosy.
Janco generated a report with data from the US Bureau of Labor Statistics. According to the February analysis, the IT unemployment rate fell from 5.7 percent in January to 5.4 percent in February.
Overall, IT employment shrank a little: about 9,100 jobs have been lost so far this year. Specifically, employers added 1,000 roles in January and 10,100 in February, according to the report. That's out of around 4.1 million IT sector jobs in the US, mind you, equating to a total loss of less than a quarter of a percent.
Security Management Best Practices
Top 10 Security Management Best Practices
- Centralize Malware Management
- Establish Boundary Control
- Centralize Provisioning and Authorization Management
- Implement Acceptable Use Policy
- Build Security into Applications Starting in the Design Phase
- Understand and implement all compliance and audit requirements
- Implement Monitoring and reporting processes
- Manage security deployment and infrastructure processes
- Implement network and host defenses
- Constantly validate network and system resource integrity
Unemployment Rate is High for IT Professionals
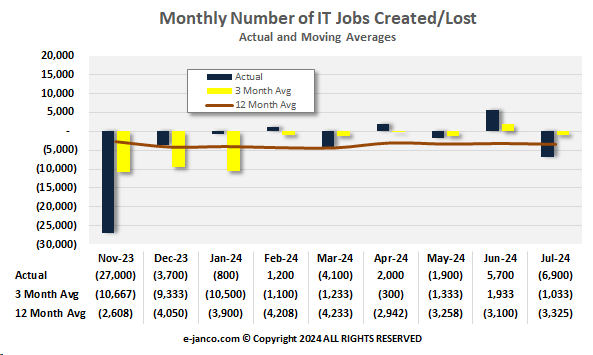
IT Job market shrank by 9,100 in the past three months
Janco reports that IT unemployment hit a new high in August as organizations shift their focus to artificial intelligence.
Six percent of IT professionals were out of work in August, up from 5.6% the month before, according to the Sept. 6 report that analyzed U.S. Labor Department data. The overall U.S. unemployment rate dipped to 4.2% in August. The IT jobless rate has surpassed the national benchmark for seven of the past eight months.
IT unemployment hasn't been this bad since the dot-com bubble burst in the early 2000s but is now being driven by a pivot from traditional IT positions to AI and cybersecurity, accordiing to Janco Associates CEO Victor Janulaitis
The roles that are most in demand right now are roles where candidates have expertise in security, AI and the cloud.
Layoffs continue in IT
Even with 4.18 million employed IT Pros layoffs continue
Layoffs are continuing as large employers of IT Pros continue to trim staff. General Motors that it is planning to cut over 1,000 software jobs. That is on top of the 4,000 plus jobs thta CSCO announced.
Read On...