Latest news of interest from Janco's news feed
Disaster Recovery Planning, Job Descriptions, Salary Survey, Business Continuity, ITSM, SOA, Compliance, SOX, and HIPAA
The Janco News feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
If you wish to subscribe to this news feed the options that you have are:
Lower salaries and fewer job openings for many IT Pros
Tools that the CIO, CSO, CTO, and CFO can use for Infrastructure, Disaster Recovery, Security, Job Descriptions, ITSM, Salary, Change Control, and Help Desk.
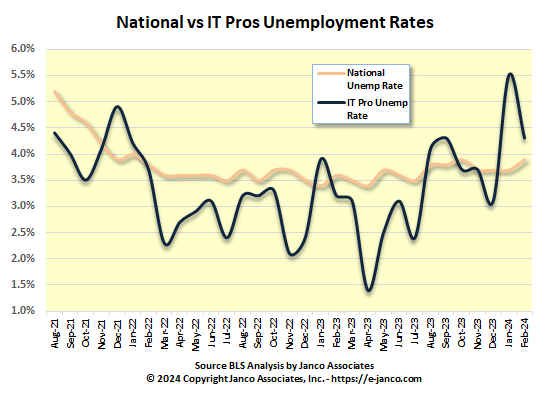
IT pros without AI skills see fewer job opportunities
The rise of artificial intelligence is affecting job seekers in tech who, accustomed to high paychecks and robust demand for their skills, are facing a new reality: Learn AI or they will not expect the same pay packages you were getting a few years ago.
The Wall Street Journal just interviewed the CEO of Janco on the prospects for IT Pros in a job market were their unemployment rates are higher than the US national rate.
Unemployed IT Pros aren't finding jobs because of a mismatch between the skills they have, AI expeience, and how much they expect to be paid. This is based on Janco's analysis, its proprietary IT job market model, and data from the BLS.
See the full story at the Wall Street Journal's website. Search on "Tech Job Seekers Without AI Skills Face a New Reality: Lower Salaries and Fewer Roles"
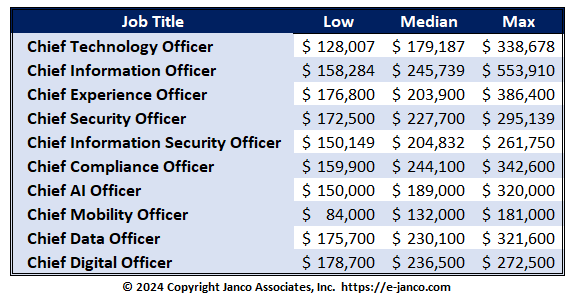
C-Level jobs on the rise in IT
Median Salary over $209K for C-level Jobs
A preliminary classification of potential reporting relationships between the c-level job title and the CIO is taken from the IT Job Classification which is published as a separate document.
As technology takes a leading role in many enterprises there are now twelve c-level titles that are appearing within many World-Class IT functions. Compensation for those positions exceeds $150K. The most frequently seen position titles are:
- Chief Information Officer (CIO)
- Chief Information Officer - Small Enterprise or SBU (CIO)
- Chief Artificial Intelligence (CAIO)
- Chief Compliance Officer (CCO)
- Chief Data Officer (CDaO)
- Chief Digital Officer (CDO)
- Chief Experience Officer (CXO)
- Chief Information Security Officer (CISO)
- Chief Mobility Officer (CMO)
- Chief Product Officer (CPO)
- Chief Security Officer (CSO)
- Chief Technology Officer (CTO)
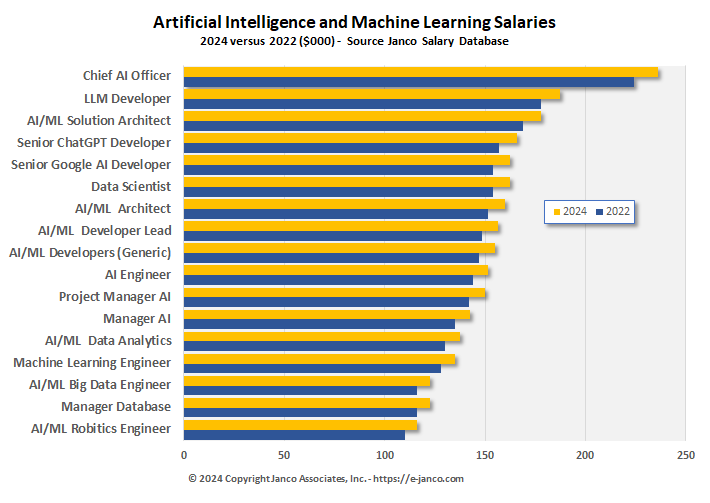
AI and ML Job Descriptions
High demand for IT Pros with AI and ML skills
Many companies have Artificial Intelligence (AI) and Machine Learning (ML) as a priority. A limiting factor is finding individuals with the skills and experience to meet those goals. Universities, over time, have provided graduates that meet the needs of businesses to meet their technological needs resources currently are not geared toward providing their graduates with the tools they need to be viable candidates for these positions.
IT Governance, ITSM, and Service Level Agreement Tools
ITSM, SLA, and IT Governance tools released
Janco has just released two offering that address the impact of the new remote workforce operating environment.
The IT Service Management Policy Template MS Word document that contains policies, standards, procedures and metrics that comply with the ITIL Standard. Chapters of the template include:
- Service Requests Policy
- Service Request Standard
- Help Desk Policy
- Help Desk Standards
- Help Desk Procedures
- Help Desk Service Level Agreement
- Change Control Standard
- Change Control Quality Assurance Standard
- Change Control Management Workbook
- Documentation Standard
- Application Version Control Standard
- Version Control Standard
- Internet Policy
- e-mail Policy
- Electronic Communication Policy
- Blog & Personal Web Site Policy
- Travel and Off-Site Meeting
- Sensitive Information Policy
- Work From Home and Telecommuting Policy
Order ITSM Template Download ITSM TOC
The IT Governance Infrastructure HandiGuide addresses the new business operation IT risks and ensures that the activities associated with information and technology are aligned with the overall business strategy.
It includes full job descriptions for Chief Technology Officer (CTO); Chief Information Officer (CIO); Chief Compliance Officer (CCO); Chief Experience Officer (CXO); Chief Security Officer (CSO); Chief Data Officer; Chief Digital Officer; Chief Mobility Officer (CMO); and Digital Brand Manager .
Security Management Best Practices
Top 10 Security Management Best Practices
- Centralize Malware Management
- Establish Boundary Control
- Centralize Provisioning and Authorization Management
- Implement Acceptable Use Policy
- Build Security into Applications Starting in the Design Phase
- Understand and implement all compliance and audit requirements
- Implement Monitoring and reporting processes
- Manage security deployment and infrastructure processes
- Implement network and host defenses
- Constantly validate network and system resource integrity
Hiring IT Pros With Certificaction is Expensive
Certifications and Salaries
Hiring the Right Staff - Key Challenge - While hiring the right people may appear more obvious in small, entrepreneurial companies, it is also true in larger companies. The right people might have the foresight to help an enterprise change and keep up with their industry. With the right people, you can move ahead and you will have a team that supports your success.
With new hires it is often difficult to validate the experience and competency of candidates being interviewed. If a candidate has formal certification, that often makes the process easier.
Several common certifications and benchmarks for starting salaries are listed.
- Certified Information Systems Security Professional (CISSP) - $100K to $135K
- Professional Scrum Master (PSM) $95K to $125K
- Amazon Web Services (AWS) certifications - $95K to $125K
- Certified Agile Leadership (CAL) $90K to $120K
- Microsoft Azure certifications - $80K to $120K
- Certified Information Systems Auditor (CISA) - $85K to $115K
- Cisco certifications - $85K to $100K
- CompTIA A+ - $65K to $90K
Ransomware Attacks Continue to Affect More Websites
Ransomware Protection is Key Element of IT Governance Infrastructure Strategy
Ransomware attacks are impacting more companies than ever. Last year over two thirds (67%) of all companies world wide suffered attacks. In 76% of those attacks, there was some data encryption that had to be addressed. The average ransom paid was $1.82 million USD.
Even if the ransom is paid, there is not guarantee the data was recovered. If is was recovered, there have been cases where the data was resold by the cyber criminals.
There is a five step process that CIOs and IT managers should follow.
- Assess risks - have a clear understanding of what they are defending against
- Implement monitoring tools - take preventive measures and implement recovery paths
- Implement essential security technologies - do not over complicate solutions
- Create a Business Continuity Plan which covers recovery from a Ransomware attack
- Train everyone on the security team - include all organization levels
Read On Order IT Governance Strategy
IT Service Management (ITSM) Service Oriented Architecture (SOA)
ITSM - SOA - Change Control - Help Desk - Service Requests Blog - Personal Web Site - Sensitive Information
When a system defect or workplace disruption hits, you need to act fast to ensure the enterprise can continue to function, your employees and associates are informed and productivity is maintained . And where better to designate the first responder than your service - help desk with a focus on IT Service Management (ITSM).
KPI metrics have taken off as measurement of the quality of IT's service has become a priority. Currently 67% of all organization have implemented the KPI approach. In a survey of 205 organizations that have these metrics in place we found that user perception is the top metric that most are focused on.
The IT Service Management Policy Template MS Word document that contains policies, standards, procedures and metrics that comply with the ITIL Standard. Chapters of the template include:
- Service Requests Policy
- Service Request Standard
- Help Desk Policy
- Help Desk StandardsITIL Service Management
- Help Desk Procedures
- Help Desk Service Level Agreement
- Change Control Standard
- Change Control Quality Assurance Standard
- Change Control Management Workbook
- Documentation Standard
- Application Version Control Standard
- Version Control Standard
- Internet Policy
- e-mail Policy
- Electronic Communication Policy
- Blog & Personal Web Site Policy
- Patch Management and Version Control Policy
- Travel and Off-Site Meeting
- Sensitive Information Policy
- Work From Home and Telecommuting Policy
EvilProxy - phishing as a service attacks
EvilProxy addressed in Security Manual Template - 2023 Edition
EvilProxy functions as a reverse proxy, where the service is positioned between the user and the real login page, relaying requests and responses back and forth between them. From the victims perspective, its like theyre interacting with the real website, but the attacker gets to see everything that gets transmitted between the two parties, including the login credentials and MFA codes. EvilProxy claims to be able to bypass MFA on Apple, Gmail, Facebook, Microsoft, Twitter, GitHub, GoDaddy, and other popular websites.
Out of hundreds of accounts that were accessed by attackers, 39% were C-level executives, 17% were chief financial officers, and 9% were presidents and CEOs. When it came to lower-level management and personnel, the attackers focused on users with access to financial assets or sensitive information.
Read on Order Security Manual Template Download sample
Supply Chain ISO Mandates defined
ISO 28000:2007 is necessary for support of an organization implementing and managing a Supply Chain Security Management System
The Security Management Standard (SMS) requirements standard, a specification for an SMS against which organizations can certify compliant.
Standard specifies the requirements for a security management system, including those aspects critical to security assurance of the supply chain. Security management is linked to many other aspects of business management. Aspects include all activities controlled or influenced by organizations that impact on supply chain security. These other aspects should be considered directly, where and when they have an impact on security management, including transporting these goods along the supply chain.
ISO 28000:2007 is applicable to all sizes of organizations, from small to multinational, in manufacturing, service, storage or transportation at any stage of the production or supply chain that wishes to:
· Establishes, implements, maintains, and improves a security management system.
· Assures conformance with stated security management policy.
· Demonstrates such conformance to others.
· Seeks certification/registration of its security management system by an Accredited third-party Certification Body.
· Makes a self-determination and self-declaration of conformance with ISO 28000:2007.
Read On...