IT Productivity Center News and Information
Metrics, Productivity, Salary Survey, Job Descriptions, Business Continuity, ITSM, SOA, White Papers, Compliance, SOX, and HIPAA
The IT Productivity Center feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
If you wish to subscribe to this news feed the options that you have are:
2024 Edition of How to Guide for Cloud Processing and Outsourcing
Tools for CIO, CSO, and CFO can use for Sarbanes Oxley, Disaster Recovery, Security, Job Descriptions, IT Service Management, Change Control, Help Desk, Service Requests, SLAs, and Metrics.
2024 Edition Includes 12 job descriptions and 7 electronic forms
The need to lower cost, increase efficiency and conserve cash has increased the motivation of companies to turn to Cloud Computing and increased the appeal of alternative delivery models. The disruptive shifts in new demand and supply patterns drives changes for how IT services are bought and from whom. Cloud computing requirements need to be well defined.
AI is one of the drivers for enterprises to select both cloud and outsourcing as an option for processing.
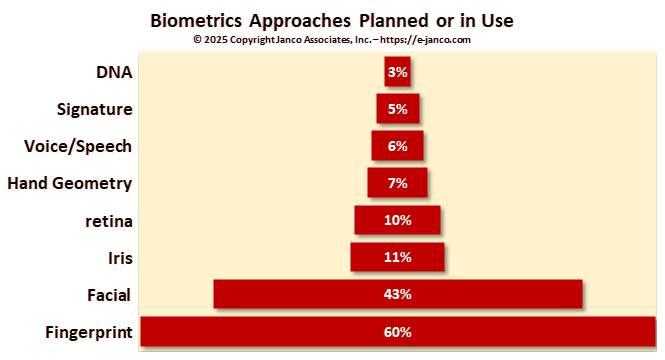
AI will speed the move to biometric security
Passwords are not as secure as biometric identifiers and via AI passwords will be replaced
Facial recognition and fingerprints are now the primary biometrics that are used. Over time, passwords will be replaced by biometrics. Currently computers and other devices have cameras, scanning capabilities, and AI capabilities which will make this shift possible.
Biometrics can be easily and accurately tied to a single individual. They do not have to be tied to any specific device. Rather they can be stored on the device itself or on an encrypted server and accessed whenever that individual needs access or use to the device, database, application, or use.
Generative AI versus Discriminative AI
KPI Metrics for Artificial Intelligence - Generative versus Discriminative
Generative AI is called generative because the AI creates something that didnt previously exist. Thats what makes it different from discriminative AI, which draws distinctions between different kinds of input. To say it differently, discriminative AI tries to answer a question like "Is this image a drawing of a car or a truck?" whereas generative AI responds to prompts like "Draw me a picture of a car and a truck on an interstate highway."
Generative AI can carry on conversations, answer questions, write stories, produce source code, and create images and videos of almost any description. The most common uses today are for answerering and routing customer service queries.
Generative AI is artificial intelligence that creates new content, including text, images, audio, and video, based on patterns it has learned from existing content. Generative AI uses machine learning to achieve the desired result. Most of that data is scraped from the internet. Programming of generative AI requires creating algorithms that can distinguish the items of interest to the AI's subjects. Generative AI creates its output by assessing large data sources, then responding to prompts with something that falls within the realm of probability as determined by resultant AI code.
Currently generative AI models are being trained with enormous volumes of data using deep learning, or deep neural networks. They can carry on conversations, answer questions, write stories, produce source code, and create images and videos of any description, all based on brief text inputs or audio prompts.
Generative AI has been around for years that was developed at MIT in 1966. But years of work on AI and machine learning have created new evolutions with the release of more robust generative AI systems. ChatGPT, a text-based AI chatbot that produces remarkably human-like prose. DALL-E and Stable Diffusion have also drawn attention for their ability to create vibrant and realistic images based on text prompts.
KPI Metrics focus on AI and new Technology
AI and Key Performance Indicator (KPI), Metrics, Quality, and Cost Control
While IT Pros'
positions -- development, engineering, administration, hand-holding -- are considered great jobs for individuals, they are also a source of unending stress and burnout. Major causes include extensive AI automation of IT Pros activities, increased workloads, excessive hours worked, lack of recognition, and lack of challenges as roles are depreciated.
AI is being used to eliminate traditional positions in IT. One classic example in IT is that of data entry and secretarial positions. Where these positions existed in every IT department in the 80s and 90s, they now are almost non-existent in the 2020s. The next group of positions that will be (or already have) eliminated are support desks with automated AI chats linked to knowledge bases for user support. Another is automated reporting of activities linked to automated alerts.
IT Professionals face more stress and anxiety with the advent of new technology like AI. Performance and productivity are driving the implementation of KPI metrics on creative and supportive tasks IT pros perform. This then is pressuring IT management to demand more from each staff member.
While there are some robust tools and platforms on the market that help automate and alleviate this pain, the growth of cloud, omnicommerce, analytics, and distributed systems have made incident response only more complex. Incidents, both major and minor, are more frequent than expected. The current way of responding to incidents is broken. AI begets more AI.
As positions are eliminated, IT managers will be looking over their shoulders to see what is next. This will add stress. We disagree with what is reported by U.S. News and World Reports that IT Pro jobs offer relatively little strain and anxiety. As AI takes hold, IT pros with be required to continually adapt to new ways they operate. That will drive stress and anxiety as described below.
- Software developer - AI will automate many of the coding processes eliminating computer programmer coding positions.
- Information security analyst - AI already is being implemented in many of the reporting functions that were traditionally gathered by IT pro and utilized to monitor and diagnose problems.
- IT manager _ Stress levels will increase as the demand for higher productivity and lower costs become the focus of executive management with the advent of AI solutions and infrastructure evolution that have AI providing new ways of doing business.
- Web developer - Website generators are now commonplace. Where it used to require programming using tools like Dreamweaver, now tools like WordPress and Sub stack have reduced the cost of entry in the "metaverse" and omnicommerce.
- Computer systems analyst - As AI moves out systems like the UPS pack theft risk assessment systems and blockchain will make individuals who have a grasp of the "big picture" more important than the granular-based individuals.
- Database administrator - Many of the traditional activities of this position are automated and included in AI-based questionnaires which drive the implementation and operation of centralized data warehouses and databases.
- Statistician - AI-based KPI reporting of information will change the role of statisticians in analyzing versus creating statistics.
Whether or not IT pros are currently stressed out in their roles, there are always solutions to stress and anxiety. CIOs can push staff to meet these new challenges, schedule changes, and more.
IT Management Tool Kit - Over 2,500 pages
CIO management concerns are constantly changing but the solutions are always centered around three factors: technology, infrastructure and people
In a recent survey of CIO and C-Level executives Janco identified the top 10 management and planning priorities that CIOs face and they relate to the three areas mentioned above.
- Security and Hacking
- Compliance
- Cost Control
- Budget Management
- Access Management
- Privacy / Identity
- Productivity of IT - Use of AI
- Mobile Computing
- Blockchain, ERP, and Cloud
- Work From Home