Information Technology and Infrastructure News
This feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is. If you wish to subscribe to this news feed the options that you have are:
IT Job Descriptions - 2024 Edition Released
CIO Resource Site News Feed
326 Job Descriptions included in the latest Edition of theInternet and Information Technology Positions Description HandiGuide
The 326 positions include all of the functions within the IT group. The Job Descriptions have been updated to be compliant with PCI-DSS, GDPR, Sarbanes-Oxley, HIPAA, CobiT, and the ITIL standards. The job descriptions are all structured to focus on "Best Practices" as defined by the IT Productivity Center to meet the requirements of World Class Enterprises. They are ready to use and easily modified to meet your enterprise's unique requirements.
Each job description is between two (2) to six (6) pages in length and has been created utilizing CSS style sheets. As such they are "out of the box" ready to use with little or no modification other than organization specific customization.
326 Internet and IT Job Descriptions as individual files in MS WORD and ePub formats. Long file names have been used to make customization easier.
Order IT Job Description HandiGuide Sample Description Download TOC
Technology Resilience and Business Continuity
Technology resilience - DRP and BCP
Technology resilience is defined as an organization's ability to maintain acceptable service levels through, and beyond, severe disruptions to its critical processes and the IT systems which support them.
Seven (7) factors C-level executives can use to get a clear grasp of what their enterprise's technology resilience is.
- Awareness is having the knowledge of what are the normal business operation requirements are; what dependencies there are on
- Protection is more than having physical and system access and security controls.
- Discovery is to know when a failure occurs.
- Preparedness means having specific action steps and plans in place to address the effects of a disruption.
- Recovery focuses on returning services and operations to business as usual levels within defined timescales and with minimal acceptable data loss following an event causing disruption or failure.
- Review and Assessment is essential for every technology resilience program, and includes post-incident reviews to identify the root causes of disruptions.
- Improvement is the process of taking the knowledge gained from all the above and taking steps to improve systems and increase resilience, and to continuously refine disaster recovery and business continuity plans.
Supply Chain Cyber Attacks on the rise
Managing a Supply Chain Security Management System (SCSMS)
A hot topic is the impact of Software supply chain (SSC) attacks with data showing these attacks rising more than 742% over the past three years.
With such continued growth, organizations continue to look for ways to mitigate the risks of SSC attacks, and various industry organizations continue to publish guidance to help organizations. The latest release comes from the US National Institute of Standards and Technology (NIST), in its special publication 800-204, also known as Strategies for the Integration of Software Supply Chain Security in DevSecOps CI/CD Pipelines.
Order Supply Chain Audit Program Download sample
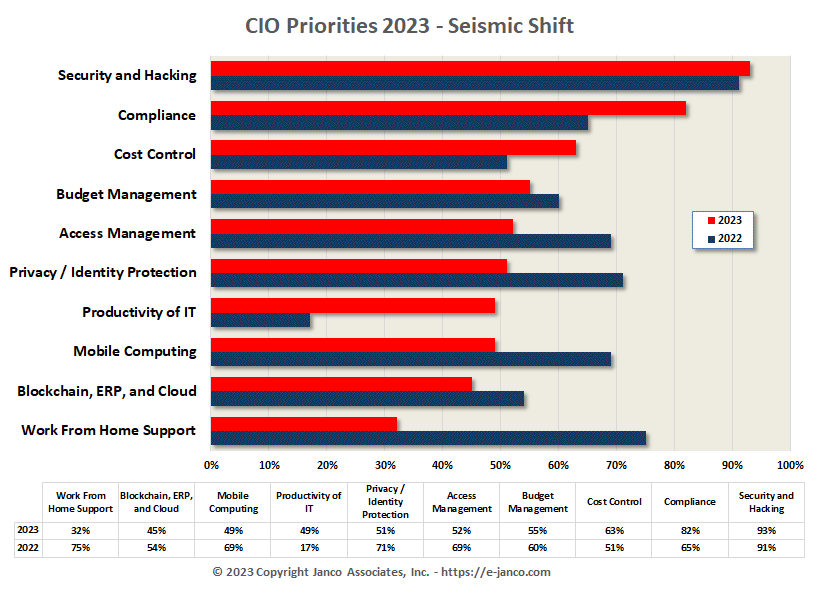
CIO Planning Priorities
Top CIO Management and Planning Priorities
Janco conducted a survey of 274 IT functions across multiple industries and from mega corporations to companies with as few as 50 IT professionals. In 2023 the top 10 priorities:
Download TOC IT Mgt Tool Kit Order IT Management Tool Kit
Top 10 Social Network Security Tips
Top 10 Social Networking Tips
Top 10 tips to improve social networking securitySocial Networking Policy
- Educate employees
- Have employees use different passwords for different system
- Mandate strong passwords
- Have employees change passwords regularly
- Do not share accounts
- Implement two factor authentication
- Educate employees to NOT open email attachments or go to links where the originator is not known
- Utilize antivirus and security software
- Don't friend people you do not know
- Validate and verify
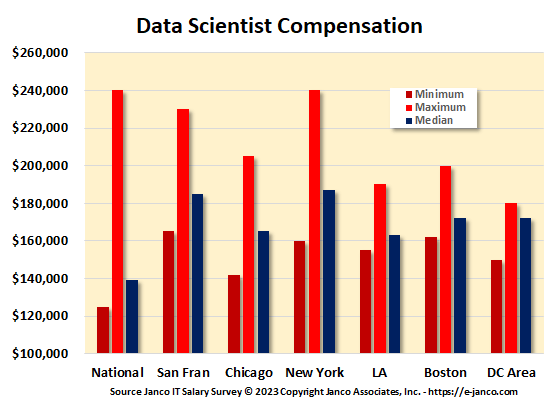
Data Scientist Job Description and Salary Data
Data Scientist Job Description
Order Data Scientist Job Description
Data Scientist Job Description - Hot New Job Title - In a recent article in the Harvard Business Review, the sexiest job of the 21st Century is that of Data Scientist. The job description created Janco has provides a clear definition of that role the individual plays in an organization.
Ransomware – IT Governance Infrastructure Key to Protection
have US Health sector targeted by Royal and BlackCat Ransomware
Royal was first observed in early 2022.They are believed to have very experienced operators, previously belonging to other infamous cybercriminal groups including Conti Team One
It is a 64-bit executable written in C++ whcih targets Windows systems by encrypting files and appends ".royal or
".royal_w" extensions to filenames and creates "README.TXT ransom note.BlackCat ransomware, AKA ALPHV, AlphaVM, Noberus, Coreid, FIN7, Carbon Spider was first detected in November 2021; per the FBI, they compromised at least 60 victims in four months. It is written in Rust; highly adaptable; Ransomware-as-a-service and conducts triple extortion (ransomware, threats to leak stolen data and distributed denial of service attacks.
IT Governance Management Team
IT Governance Management Team job descriptions
To support the process the IT Governance HandiGuide includes ten (10) full job descriptions: