Microsoft, Windows, and Internet News - XML News Feed
Microsoft, Windows, and Internet News - XML News Feed - The Internet and Mobility News feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
If you wish to subscribe to this news feed the options that you have are:
Is BLS data being manipulated?
A management site for IT
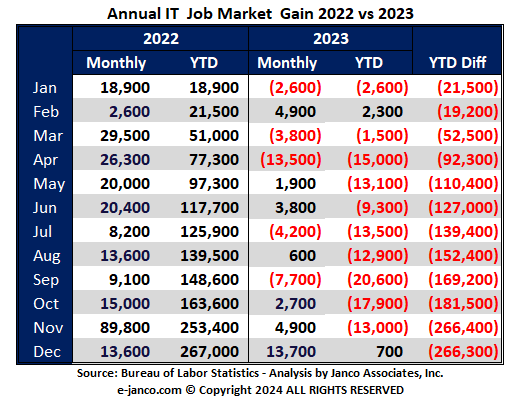
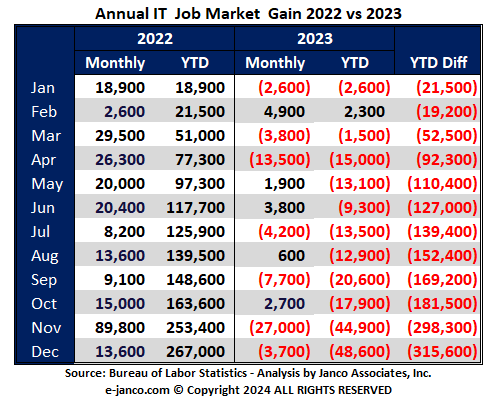
BLS cuts the number IT jobs from the initially reported
The BLS continues to adjust the number of IT jobs initially created in previous months. They have adjusted down by over 13,000 jobs in seven of the last 12 months. This in turn inflates the number of jobs reported in the current month.
The BLS adjusted the number of IT jobs initially reported for December and November. They updated the number of jobs initially added in December (reduced number jobs) and January (reduced mumber jobs).
Before Adjustment
After adjustment
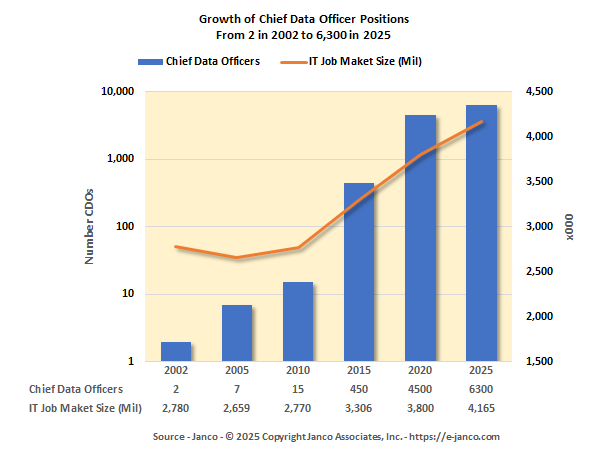
Chief Digital OfficerJob Description Released
Chief Digital Officer Now in over 50% of all enterprises
The most mature and most data-fluent organizations are now using data to determine new business opportunities and new products to develop as well as how to be more efficient, more productive and more competitive. CDO's purpose is to break down barriers that remain between IT, the data function and the business units.
Read On Chief Data Officer Order Chief Data Officer Job Description
AI and Machine Learning IT Pros are in Demand
AI Expertise goes mainstream with the moves towards the Artificial Intelligence and Machine Learning
AI and Machine Learning Specialists top the list of fast-growing jobs. Next are Sustainability Specialists, Business Intelligence Analysts and Information Security Analysts, and Renewable Energy Engineers.
Prompt engineers can earn a six-figure salary - up to $335,000 a year. That's because prompt engineering is needed to improve human-machine interaction with genAI tools; learning about the foundational technology - large language models (LLMs) - provides the best possible responses to queries.
The Manager AI provides the strategic direction on compliance for the design, development, and implementation of AI models into operational workflows, including helping draft and review the procedures that support a compliance system. Additional responsibilities may include guiding AI teams with project planning, system architecture, risk management, verification & validation, and continuous monitoring.
Data Security - Top 10 Best Practices
Security Best Practices
There are best practices that CIOs need to implement in order to protect a businesses' data:
- Understand who is accessing data via frequent auditing and real-time monitoring of data access
- Keep current records on data access permissions
- Classify data by sensitivity
- Minimize and remove global access rights
- Identify data owners and users
- Include data access reviews when individuals are transferred, promoted, or terminated
- Align groups to data ownership and management
- Audit permissions and group changes
- Lock down, delete or archive stale, unused data
- Clean up security groupings
ISO 28000 Supply Chain Security
ISO 28000:2007 is necessary for support of an organization implementing and managing a Supply Chain Security Management System (SCSMS)
With companies that have a high reliance on just-in-time delivery, aging infrastructure and increased natural and human-made threats. As a result Supply Chain Security has become a very important item for them, especially when viewed in relation with Business Continuity Management, Risk Management and Security Management.
Safety Liability for WFH employees
Safety Program defined for WFH
Janco's Safety Program HandiGuide delivers a comprehensive solution for safety compliance, combining its knowledge of the broad spectrum of risks, mandated compliance requirements and the drive to continuously improvement the safety culture across the entire workplace.
Cost of Cloud Outage
Cost of Cloud Outage
Cost of outage is very expensive. If a business has 50,000 customers and just 10% reach out to complain, that's 5,000 complaints to address. That is a significant loss time and energy that could have been spent acquiring new customers and growing the business.
Those unhappy customers are also likely to share their less-than-positive experiences with friends and family, in person or through social media, and might move on to do business with competitors.
Experts estimate that the cost of losing critical applications is more than $5,000 per minute. Nearly 20% of the surveyed companies indicated losses of between $50,000 to over $5,000,000 after losing critical applications and/or data.
Unseasoned remote workers put companies at risk
IT Mobility Policy Bundle can help companies stay safe as more employees work from home
Allowing remote employees to connect to and access critical infrastructure without having proper authorization, authentication and accountability in place significantly increases the risk of cybercriminals misusing that access. The current cybersecurity skills shortage coupled with small cybersecurity budgets and the security challenges brought forward by remote employees can spell disaster for SMBs.
It is one thing to say that workers will work remotely and access sensitive and confidential information via the internet. It is quite another to be able to assure executive management that critically sensitive information is protected and compliance mandates are met.
Video Conferencing US Govermement Mandates - FEDRAMP
FedRAMP Program Management Office (PMO) mission is to promote the adoption of secure cloud services across the Federal Agencies
In doing business with the US Federal goverment suppliers of cloud based servvice need to comply with FEDRAMP. The FedRAMP Program Management Office (PMO) mission is to promote the adoption of secure cloud services across the Federal Government by providing a standardized approach to security and risk assessment.
In support of this the US National Security Agency (NSA) published a questions to ask before using one of today's popular video conferencing, text chatting, and collaboration tools. The 8 point list includes:
- Does the service implement end-to-end (E2E) encryption?
- Does the E2E encryption use strong, well-known, testable encryption standards?
- Is multi-factor authentication (MFA) available?
- Can users see and control who connects to collaboration sessions?
- Does the tool's vendor share data with third parties or affiliates?
- Do users have the ability to securely delete data from the service and its repositories as needed (both on client and server side)?
- Is the tool's source code public (e.g. open source)?
- Is the service FedRAMP approved for official US government use?
Order IT Infrastructure Policies Download TOC
Omni Commerce new e-commerce paradigm
Enterprises are now moving towards the new e-commerce paradigm
SmartPhones and tablets are changing the way the way people and business browse the Internet, shop, provide service and communicate with suppliers, customers and associates.
CIOs need to have the right foundation. Leadership begins with having a strategy in place that works and then having the right people in place to create and implement the,.
Order Omni Commerce Planning Toolkit
Download Selected Pages Omni Commerce Strategy