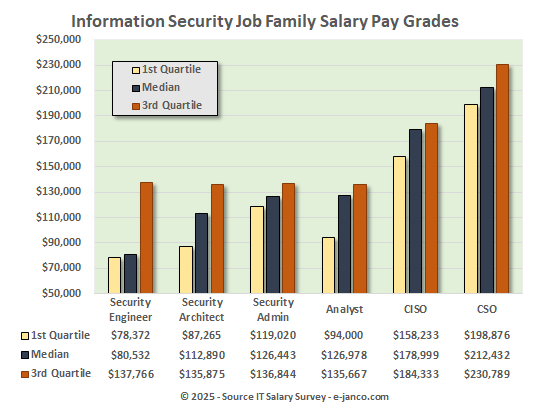
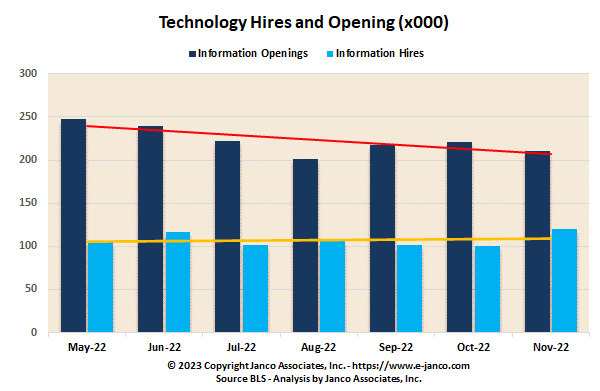
Chief Information Officer and IT Managers Areas of Interest
Disaster Recovery Planning, Job Descriptions, Salary Survey, Business Continuity, ITSM, SOA, Compliance, SOX, and HIPAA
Chief Information Officer and IT Managers Areas of Interest - The CIO and IT management news feed is one that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
If you wish to subscribe to this news feed add the link below to your reader:
Computerworld quotes Janco employment report
CIO and IT Manager news articles
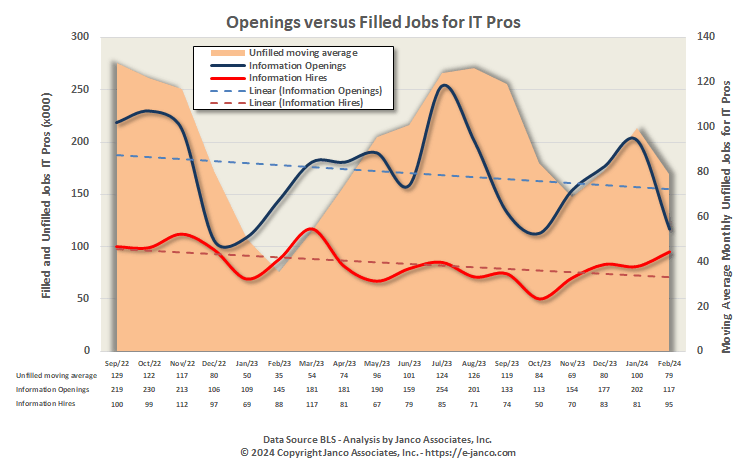
4.18 million individuals are employed as IT Pros in the US
Janco's employment report was quoted in a Computerworld article.
"... lackluster IT job market performance in February. It said in its report today that hiring of IT Pros is hindered by the lack of qualified individuals and a slowing economic picture, which will have a dampening impact on the growth of the IT job market size."
"...there are currently 4.18 million US workers employed as IT professionals. The rate of growth in the number of new IT jobs has slowed..."
"There now are just over 121,000 unemployed IT professionals. The IT job market shrank by over 48,600 jobs in calendar year 2023, Jancos report stated. Overall that is a flattening of the long term growth rate pattern of IT job market.."
"One of the more surprising results of the BLS report, however, was that the agency drastically revised its January job gains, which had previously been reported as a leap of 353,000 new jobs. The revised numbers dropped that by more 124,000 jobs."
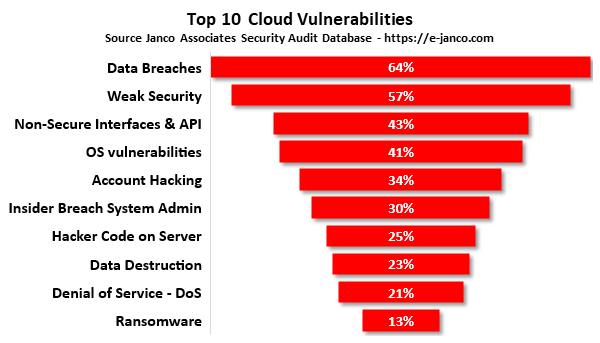
IT Governance addresses top 10 security vulnerabilities
IT Governance addresses cloud processing security and compliance vulnerabilities
IT Governance Infrastructure HandiGuide by Janco addresses top 10 cloud security vulnerabilities.
- Data breaches
- Weak Security
- Non-Secure Interfaces & API
- OS vulnerabilities
- Account hijacking
- Insider breach as System Administrator
- Parasitic code on server
- Data Destruction -
- Denial of service (DoS)
- Ransomware
Disaster Recovery Planning & Business Continuity Planning Quick Action Steps Defined
The must do things that your company must do to make sure the disaster recovery and business continuity plan will work when they are need are:
Distribute the disaster recovery and business continuity plan or a HandiGuide® to all decision makers and key operating employees who will need access to it when the event occurs.
Bank Payment and Check Washing Scams are on the Rise
Cybersecurity Management
Two finance and bank-related swindles are starting to rise. Everyone needs to be aware and follow best practices.
Pay Yourself Scam
Scammers mine for PIN data of consumers through phone calls, emails, text messages, or social media messages. They use spoofed phone numbers or email addresses that appear legitimate, making it seem like they are indeed from a trusted bank. Common scam tactics.
The Pay Yourself scam begins with a text message from a scammer that looks like a fraud alert from their bank. If the individual responds to the text message and engages the scammer, they get a call from a number that appears to be from their bank. The scammer impersonates a bank employee and offers to stop the alleged fraud. The scammer is tricking the user into sending money to their bank account.
When you enroll in a service they recommend like Zelle, the bank sends the individual a security code to verify their identity. The scammer claims that they need this passcode to authorize your payment to yourself.
If the code is provided, then the individual will provide them with the keys to their account. With that passcode, the scammer is able to connect the individual's bank account with Zelle utilizing the individual's email or phone number. The money the individual thought they were sending to themself is sent directly to the scammer's bank account.
Check Washing
According to the United States Postal Inspection Service (USPIS), check washing is growing at an alarming rate thanks to bands of thieves who fish personal checks from USPS mailboxes or take them out of personal mailbox. They may even go as far as robbing mail carriers in search of checks.
USPIS says it recovered more than $1 billion in counterfeit checks and money orders in the last 12 months.
Once they have a check you wrote and mailed -- for example, to a charity -- they use chemicals to wash the check to change the amount or make themselves the payee. They then deposit the individual's check and steal money from their account. A warning sign is If a check which was mailed that was paid, but the recipient never received it, the individual may be a check-washing victim.
Ways to a mitigate this scam are
- Consider making payments using e-check, ACH automatic payments and other electronic and/or mobile payments.
- Use pens with indelible black ink so it is more difficult to wash the checks.
- Follow up with charities and other businesses to make sure they received the check.
- Use online banking to review copies of checks to ensure they were not altered.
- If you still receive paid checks back from the bank, shred dont just trash them.
- Regularly review bank (and credit card) activity and statements for errors.
- Don't leave blank spaces in the payee or amount lines of checks you write.
- Drop off mail in blue collection boxes before the last scheduled pick-up time or directly at your local Post Office.
- Regularly check your mail. Do not leave your mail in your mailbox overnight.
- If you are heading out of town, have the Post Office hold your mail or ask a trusted friend or neighbor to pick up your mail.
CIO and HR Staff Management Kit
Economic Turmoil Mandates Aggressive Management of Staffing
Every CIO and IT organization that is successful has the right organization and staffing in place. The basis of that is an organization with clear definition of responsibilities, compensation that is competitive, and clear career paths which all IT professionals can relate to.
The CIO HR and Staffing Management Kit contains the tools needed to support the CIO and the IT department in its quest to get and maintain the best IT talent.
The CIO HR and Staffing Management Kit is provided in MS WORD, PDF, and ePub formats. Included are the following
- Internet and IT Job Descriptions HandiGuide
- All of the Job Descriptions
- IT Job Classification & Pay Grade HandiGuide
- Interview and Hiring Guide
- Termination Checklist (electronic form)
- Latest IT Salary Survey (PDF format only)
Read On CIO HR Staffing Management Kit Download Selected Pages
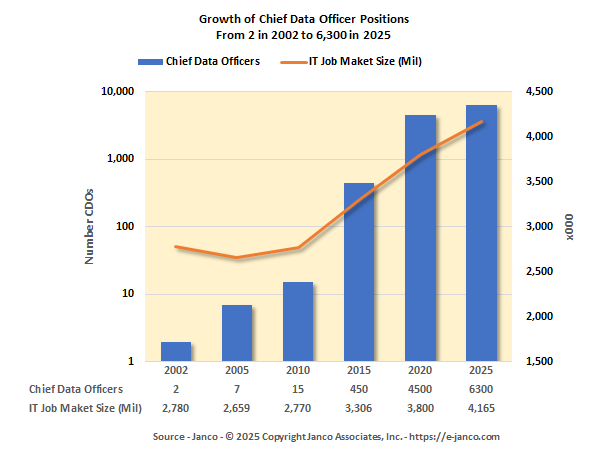
Chief Data Officer (CDO) Job Description
The Chief Data Officer job description has just been updated.
Chief Data Officer (CDO), a newly created postion, is responsible for developing and overseeing data strategy and governance for the enterprise.
The CDO is not only a data expert but also a seasoned operational manager. As the role is transformational, the CDO is responsible for the adoption of data technologies across the entire business. As with most senior executive titles, the responsibilities are set by the organization's board of directors or other authority, depending on the organization's legal structure.
Growth in the number of CDO's has been dynamic. There now are over 4,500 individuals filling that role today.
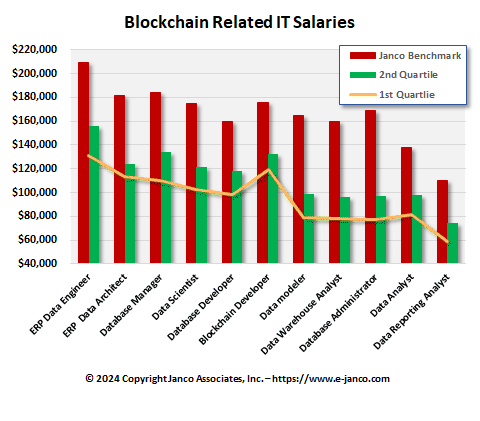
Blockchain Job Descriptions
Available for Immediate Download - Blockchain Job Descriptions
The major part of the blockchain and cryptocurrency jobs market remains to be focused on developers, and this continues to be the area of most demand. The "U.S Emerging Jobs Report" published by Linkedin shows that demand for blockchain developers has grown 33 times over the previous year.
The average salary for a blockchain developer was reported to be $127,000, according to Janco Associates, a consulting firm that conducts salary surveys.
Chief Experience Officer Job Description
Chief Experience Officer (CXO) Job Description
Chief Experience Officer (CXO) drives the enterprise's growth in the user experience arena. They oversee operations in all user experience sectors like marketing, image setting, mobile applications, social media, related technologies, and virtual goods, as well as web-based management and marketing.
Even with a starting salary that can exceed $175K, the Chief Experience Officer (CXO) is one of the hardest to fill. It is the one position that is responsible for setting and operating the foundation of how an enterprise presents itself to the outside world.
How do layoffs impact IT Pros
Hiring of IT Pros Slowing are ayoffs take hold
Layoffs have far reaching impacts on both the people ware are laid off and those who remain.
- 66% of layoff survivors report they feel overworked after the layoffs, and a third of those who survived a layoff believe that things will worsen for their company.
- 81% of layoff victims say they experienced at least one symptom of depression after losing their job, and 73% struggle financially.
- 83% of CIOs and CFOs believe layoffs are the right decision to make in recessionary times
- 69% of layoff victims didn't receive any form of support from their former employers.
- 60% of layoff victims are less likely to trust their next employers.
Over 4 Million individuals are employed as IT Pros in the US
Hiring of IT Pros Robust but Slowing
Hiring of IT Pros is hindered by the lack of qualified individuals. This will have a dampening impact on the growth of the IT Job Market size.
Order Salary Survey Download Sample