Threat Vulnerability Assessment 2025 Edition
Artificial Intelligence Solutions Added
Job Descriptions for Chief AI Officer and Chief Security Officer (CSO) included
Electronic Forms and Design Files easily modified for distribution and management of the risk assessment process - Addresses Ransomware
Threat and vulnerability assessment are key to planning for and being prepared before an adverse event occurs
Order Threat Vulnerability Tool Download Selected Pages
 Threat Vulnerability Assessment Tool - The purpose of a Threat Risk Assessment (TRA) is to categorize enterprise assets, examine
the different “threats” that may expose an enterprise to risks, and identify and correct the most immediate and obvious
security concerns. While taking tactical measures to
correct immediate problems is important, understanding the different threats and risks will enable management to make informed decisions about security so they can apply appropriate, cost effective safeguards
in the longer term. This balanced approach allows for
strategic positioning by logically applying risk mitigation strategies in a controlled and economical manner
rather than “informal” and often expensive implementations
Threat Vulnerability Assessment Tool - The purpose of a Threat Risk Assessment (TRA) is to categorize enterprise assets, examine
the different “threats” that may expose an enterprise to risks, and identify and correct the most immediate and obvious
security concerns. While taking tactical measures to
correct immediate problems is important, understanding the different threats and risks will enable management to make informed decisions about security so they can apply appropriate, cost effective safeguards
in the longer term. This balanced approach allows for
strategic positioning by logically applying risk mitigation strategies in a controlled and economical manner
rather than “informal” and often expensive implementations
This tool includes Artificial intelligence (AI) threat and risk assessment in a systematic process to identify, evaluate, and mitigate potential risks associated with AI systems, ensuring their responsible and secure deployment. This involves a structured approach across domains like security, privacy, fairness, and accountability, with strategies and tools to manage AI risks throughout their lifecycle, and frameworks.
 Janco's threat, risk and vulnerability assessment is an objective evaluation of threats, risks, and vulnerabilities in which assumptions and uncertainties are clearly considered and presented. Part of the difficulty of risk management is that measurement of both of the quantities in which risk assessment is concerned - potential loss and probability of occurrence - can be very difficult to measure. The chance of error in the measurement of these two concepts is large. A risk with a large potential loss and a low probability of occurring is often treated differently from one with a low potential loss and a high likelihood of occurring. In theory, both are of nearly equal priority in dealing with first, but in practice it can be very difficult to manage when faced with the scarcity of resources, especially time, in which to conduct the risk management process.
Janco's threat, risk and vulnerability assessment is an objective evaluation of threats, risks, and vulnerabilities in which assumptions and uncertainties are clearly considered and presented. Part of the difficulty of risk management is that measurement of both of the quantities in which risk assessment is concerned - potential loss and probability of occurrence - can be very difficult to measure. The chance of error in the measurement of these two concepts is large. A risk with a large potential loss and a low probability of occurring is often treated differently from one with a low potential loss and a high likelihood of occurring. In theory, both are of nearly equal priority in dealing with first, but in practice it can be very difficult to manage when faced with the scarcity of resources, especially time, in which to conduct the risk management process.
One of the problems of computer security is deciding on how much security is necessary for proper control of system and network assets. This gets down to the concept of threat assessment or, more specifically, what do you have and who would want it? While it sounds relatively simple to state, it's not that easy to assess corporate network threat unless you approach things in a structured manner.
The Threat Vulnerability Assessment Tool
Janco's Threat Vulnerability Assessment Tool is one component of a series of HandiGuide™ Tools that have been created by Janco for use by enterprises of all sizes. Some of the drivers behind the Threat, Risk and Vulnerability Assessment Tool are requirements like those mandated by GDPR,CCPA, Sarbanes Oxley, HIPAA, ISO, and PCI-DSS.
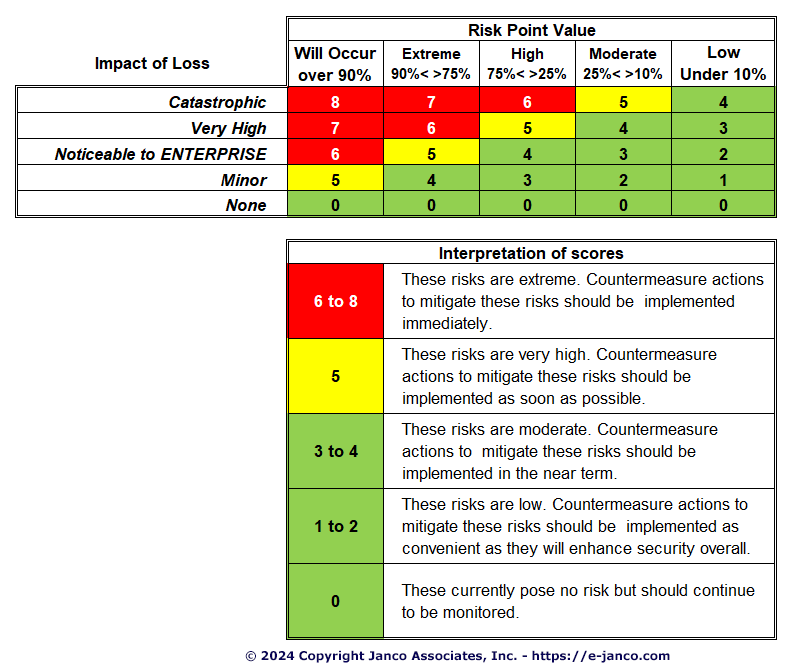
For example, most compliance mandates require enterprises to conduct a risk vulnerability and threat vulnerability assessment at least annually. The process concludes with a security vulnerability assessment. Below is a sample of a risk assessment created with the Threat Vulnerability Assessment Tool.
Sample Risk Assessment
The Tool comes with a work plan that can be used to conduct the Threat and Vulnerability Assessment as well as a definition of the components of the process including:
- Administrative Safeguards
- Logical Safeguards
- Physical Safeguards
- Six (6) full job descriptions
- Chief Artificial Officer (CAIO)
- Chief Security Officer (CSO)
- Manager Artificial Intelligence
- Manager Compliance
- Manager Sarbanes-Oxley Compliance
- Manager Security and Workstations
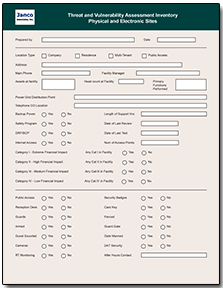
- The electronic form is included along with the design file making it easily modifiable. The form is designed and is easily completed completed for each physical
location of the enterprise and for each functional operation and location. Sections of the Tool
include the following:
- Demographics of each physical location,
- Access to each facility at each physical location,
- Environmental factors associated with each physical location,
- IT and business process at each,
- A risk ranking
matrix with a scoring mechanism that looks at:
- Vulnerability as measured by probability of the threat occurring
- The impact of the loss
- Rules for scoring the risk