Browser and Operating System Market Share White Paper
Firefox - IE - Opera - Mozilla - Safari - Google Chrome
The Browser Market Share and Operating System Market Share White Paper data is by month starting in September 1997 through the February 2010. The data sampled is internationally based (Just under 50% of the data points sampled are outside of the United States).
February 2010 Browser and OS Market Share Study Released
Janco has released its latest Browser and OS Market Share White Paper. One of the major findings is the difference in acceptance of Windows 7 versus the the acceptance rate of Vista.

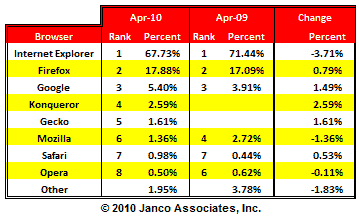
February 2010 White PaperIn the last several months Microsoft's browser market has continued to decay. Firefox and Google (Desktop and Chrome) continue to have the potential to eat away at the Microsoft browser monopoly. Users who move to Vista and Windows 7can more readily have multiple browsers on their systems and switch from one to the other quickly and with little pain. In addition with the release of the browser ballot option for the EU we forecast there will be a continual erosion of Microsoft's IE market share. Based on our test results current versions of IE and Firefox are significantly more robust than prior versions. In addition, IE 8 is feature rich and a step ahead of the other browsers. Chrome has major defects which limits its usefulness on all sites. Several of these defects are highlighted in this White Paper. Trends in Browser Market Share
|
Microsoft IE Market Share History
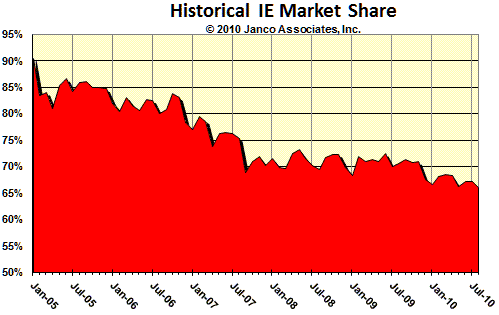
Browser Twelve Year Historical Trend
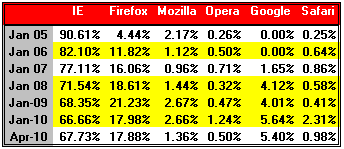
This data is updated in the full study. The full study was produced with data through February 2010. See a full copy of the press release here.
Browser and Operating System Information
Intel can not meet chip demand
As companies upgrade to Windows 7 and replace older laptops there is a shortage of the latest Intel laptop PC Core i3 and Core i5 microprocessors.
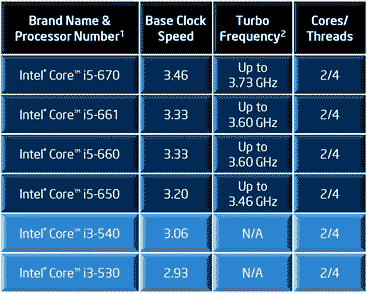
The shortfall is in Intel's new laptop microprocessors codenamed Arrandale, including some Core i3 and Core i5 chips. The shortage has caused chip buyers to bid the price of the microprocessors up to a 20 percent premium over contract prices on the open market, according to U.S. chip distributor Converge. The shortage hit in March and will last throughout April, the company added in a monthly research report.
- more infoRecord Management Needs to Include Email
As the importance of IT, the Internet, SmartPhones, and email has grown, its legal status has changed with far-reaching consequences. A variety of laws and regulations have been extended to cover all business records, including email and all communications in both public and private sectors. Sarbanes-Oxley (SOX) and other mandates requirements touch almost every facet of paper and electronic data.
Among other provisions, SOX requires companies to maintain ?all audit or review work papers? for at least five years. For registered public accounting firms, the period is at least seven years. Penalties for noncompliance include severe fines and even imprisonment, and intentionally altering or destroying records can bring even more serious consequences.
Consider that most work papers and records are created as emails and may never exist in physical form. An email can be deleted in violation of SOX at the click of a mouse. Key considerations for ensuring your company meets SOX record-keeping requirements include:
- Can employees reliably distinguish ordinary emails from protected business records?
- Are you be certain that employees are storing the protected emails for the required time period?
- Is there a process in place for storing physical copies of every protected business records and emails?
- Are you certain that no one is hacking into your email system and maliciously changing records?
Utah may extend the reach of e-verify
The Utah state legislature has pass SB 251 to its governor, which would require businesses with 15 or more employees to use E-Verify to check whether new hires are legal workers, passed the legislature this month and is waiting for action by Governor Gary Herbert. However, some activists report the bill may be in trouble because business lobbies are working hard to get the governor to veto the bill.
- more infoDatabase security a management issue
Traditional IT security focuses on protecting the corporate network perimeter with firewalls, VPNs, and antivirus software. While important, these first-line defenses aren't enough. New technology and business practices spread sensitive data across multiple channels, creating new vulnerabilities. The solution is safeguarding data where it lives - in the database and on the file servers. - more infoSecurity Policies Should be Part of Normal Business Practices According to Federal Judge
 A federal judge has
rejected a proposed settlement by TD Ameritrade Inc. in a data breach lawsuit. That marks the second time in recent months that a court has weighed in on what
it considers basic security standards for protecting data. The case stems from a
2007 breach that exposed more than 6 million customer records.
A federal judge has
rejected a proposed settlement by TD Ameritrade Inc. in a data breach lawsuit. That marks the second time in recent months that a court has weighed in on what
it considers basic security standards for protecting data. The case stems from a
2007 breach that exposed more than 6 million customer records.
The federal judge did not find the proposed settlement to be "fair, reasonable, or adequate. " Rather than benefiting those directly affected by the breach, Ameritrade's proposed settlement was designed largely to benefit the company. The judge described the additional security measures that Ameritrade proposed in the settlement as "routine practices" that any reputable company should be taking anyway and should be defined in their normal security policies and procedures.
In September 2007, Ameritrade said that the names, addresses, phone numbers, and trading information of potentially all of its more than 6 million retail and institutional customers at that time had been compromised by an intrusion into one of its databases. The stolen information was later used to spam those customers.
As part of an effort to settle claims arising from that incident, Ameritrade this May said it would retain an independent security expert to conduct penetration tests of its networks to look for vulnerabilities.
The company also offered to retain the services of an analytics firm to find out whether any of the data that had been compromised in the breach had been used for identity theft purposes. The company also said it would give affected customers a one-year subscription for antivirus and anti-spam software.
- more info