Denial of Service Attacks on the Rise!!!
 Denial-of-service attacks are not new, but the rapidly increasing number of attacks is making bot-nets a formidable security threat. Here are six things to keep in mind as you secure your networks.
Denial-of-service attacks are not new, but the rapidly increasing number of attacks is making bot-nets a formidable security threat. Here are six things to keep in mind as you secure your networks.
- What you see is not always what you get. Determining the source of an attack is challenging. The so-called North Korean attacks in July appear to have been controlled from a server in the United Kingdom. Remember, just because an attack originates in one country does not mean it is managed from there.
- Money changes everything. Money is a motivator as underground developers are selling tools such as an on-line service to run new malware variants against the most popular anti-virus engines to identify which ones make it through. With bot-net tools for sale, relative amateurs can launch sophisticated attacks.
- It is no longer just kids. Professionalism is on the rise. The most serious attacks can go undetected as bot-nets designed to steal data or tap computing power have gotten better at encryption and covering their tracks.
- It is not the medium, it is the message. Be as suspicious of embedded tweets and videos as you are reviewing your e-mails.
- Eternal vigilance is the price of liberty. Consider real-time content analysis as a weapon in defending your networks.
- New world order. Get used to them -- they are here to stay. New attacks are emerging at a faster and faster pace, so the need to update security is paramount.
Read on Order Security Manual Template Download sample
Data Breaches Continue to be CIO Concern
The FBI received a record number of complaints in 2008, and the associated direct cost of the frauds carried out with stolen data was $265 million versus $235million in 2007. Adding to this is the challenge of securing personal information and intellectual property data. Companies are granting access to more systems and information - bank customers access to account balances; workers maintain their own 401k and investment accounts; web shoppers place orders and make purchases with a single click; and business partners work on projects in a collaborative manner on line.
To reduce the risk of a data breach or theft, organizations must adopt new tactics. In addition, companies must address e-mail and Web security along with employing a functional data loss and prevention strategy. The application of multiple security techniques is required to reduce risk. For example, there must be a way to control spam and block the downloading of malicious software from poisoned Web sites. In today's open Web 2.0 and social networking environments, companies need a way to defend against attacks and protect secret or sensitive data. At the same time, they must maintain a flexible and responsive infrastructure to support today's business working habits.
The Janco Security Manual Template has helped over 2,000 enterprises world-wide to meet these requirements.
Read on Order Security Manual Template Download sample
Are you paying too much or too little to your information technology staff?
Are you earning what you're worth? Whether employer or employee, it is important to know what other companies are paying in total compensation for a similar position in your area. Learn how your company compares in the area of compensation. Data as of June.
NOTE: the table below is updated automatically with the latest IT salaries when a new salary survey is published. That happens every January and June. The historical data is available.
Latest Median IT Salaries
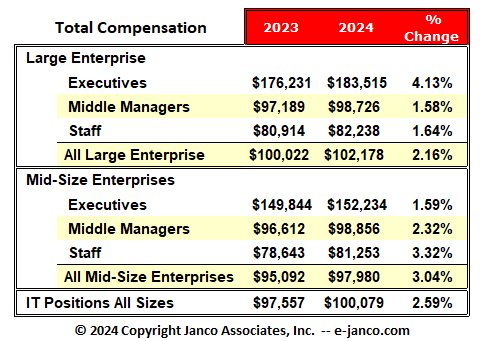
For the latest data go to the current IT Salary Survey
Read on Salary Survey Order Salary Survey Download Summary





