E-mail Threats - The Ransomware Gateway
E-mail is still the gateway used by Ransomware Cyberattackers
 Email cyberattacks are as old as email itself. Attackers continue developing new tactics as security capabilities continue to become more robust. While ‘click-and-run’ attacks like spam and mass phishing campaigns still exist, attackers don’t spend too much time crafting them and they can be effectively blocked with traditional security controls.
Email cyberattacks are as old as email itself. Attackers continue developing new tactics as security capabilities continue to become more robust. While ‘click-and-run’ attacks like spam and mass phishing campaigns still exist, attackers don’t spend too much time crafting them and they can be effectively blocked with traditional security controls.
Cyberattackers have now moved towards email attacks that evade metadata-based detection, don’t have binary ‘good or bad’ payloads, and are finely crafted to push all the right psychological buttons of their intended victims. These attacks, broadly classified under the Business Email Compromise (BEC) umbrella, with ransomware, have moved into the area of mainstream C-Level management concerns. The 2019 Internet Crime Report IC3 from the Federal Bureau of Investigation found that over $26 billion has been lost in Business Email Compromise (BEC) attacks between 2016 and 2019.
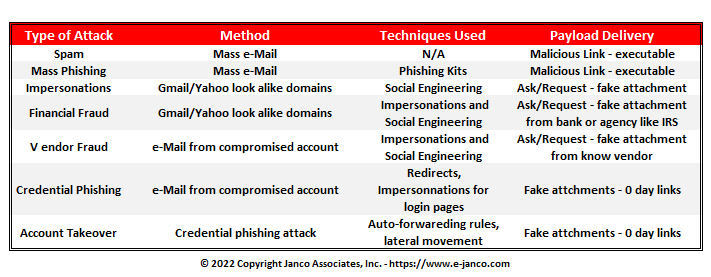
The new email attacks usually share these characteristics:
- Driven by targeted research - Targeted attacks avoid the scattergun approach of mass phishing attempts and are the result of extensive groundwork and research conducted by the attacker. The attacker is aware of the victim’s name, job title, reporting manager, and sometimes even what days they’ll be out of office.
- No malicious payloads are contained in the initial email - Targeted attacks rarely include URLs or attachments that contain known malicious payloads, especially in the first email. Payloads may sometimes be introduced at the end of email chains after the attacker has gained the victim’s trust. It’s more likely for the ‘payload’ to be within the email content itself i.e. requests that are framed like they’re coming from a legitimate individual known to the victim.
- E-mail rules and metadata are not enough - Since targeted attacks are more focused on their technique, metadata and binary rules are not enough to flag these emails. These protection techniques either lead to a flood of false positives (if they’re too strict) or let finely crafted attacks escape their grasp (if they’re not strict enough).
- Emails are socially engineered - Targeted attacks prey on human nature as much as - if not more than - security controls. Leaning on age-old psychological tricks like urgency, authority, persuasion, and fear, the language in these emails makes the victims ‘want’ to take action without thinking too much about it.
Order email communication Policy Download Policy Selected Pages


