Security Manual - Tools for CIOs and IT Managers - DRP Template
Over 326 IT Job Descriptions
Disaster Recovery Plan Template, DRP Template, DRP Sample, Security, Job Descriptions, and Infrastructure Tools
Tools for enterprise CIO and IT Managers - DRP Template - IT job Descriptions Infrastructure Policies - IT Governance - Tools for the CIO and IT Managers. BCP and DRP Template, IT Job Descriptions, Policies, and Cyber Security Manual are delivered electronically.
Disaster Recovery Business Continuity |
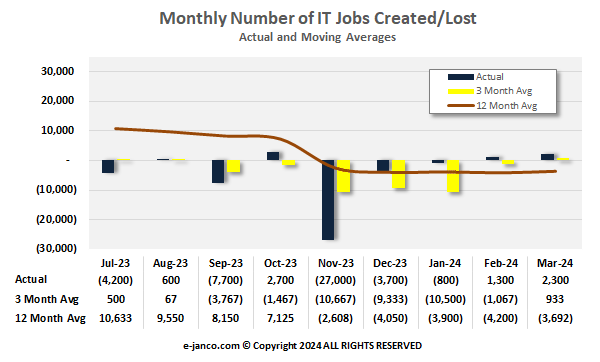
Monthly Job Market Growth |
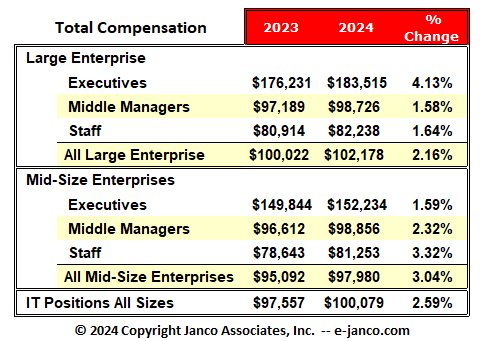
2024 IT Salary Survey Released
IT Professionals are paid more in large enterprises than in SMBs. For the first time, median salaries for all IT pros in large enterprises exceed $100K. Most of the highest salaries are for the IT executives in those enterprises.
Read on Salary Survey Order Salary Survey Download Summary
2024 Internet and IT Position Description HandiGuide Released
 There are now 326 IT Job Descriptions available that that have been updated to meet the latest compliance and new technology requirements. The HandiGuide can be acquired in MS WORD and / or PDF format. In addition we provide the option to get updates and free custom job descriptions.
There are now 326 IT Job Descriptions available that that have been updated to meet the latest compliance and new technology requirements. The HandiGuide can be acquired in MS WORD and / or PDF format. In addition we provide the option to get updates and free custom job descriptions.
Recently added job descriptions include:
- Chief AI Officer
- Chief Experience Officer
- Chief Information Security Officer
- Chief Product Officer
- Digital Content Specialist
- Manager Artificial Intelligence
- Manager Blockchain Architecture
- Project Manager Blockchain
- Blockchain Analyst
- Manager DevOps
- Manager Telecommuting
- Manager WFH Support
- DevOps Job Family
- System Analyst Job Family
- Full Stack Developer
- Web 3 Analyst
- Web 3 Developer
All of the positions in the book are gender-neutral and have been created to reflect technical competencies, jobs proficiency levels and meet compliance requirements of 2024.
Disaster Recovery and Business Continuity - 2024 Edition Available
Cloud DR/BC Supported in the 2024 Edition
 The Disaster Recovery Business Continuity Template is a comprehensive tool and set of disaster and business continuity planning resources, including a detail disaster recovery business continuity work plan on how to proceed from evaluating risk factors to retrieving server data.
The Disaster Recovery Business Continuity Template is a comprehensive tool and set of disaster and business continuity planning resources, including a detail disaster recovery business continuity work plan on how to proceed from evaluating risk factors to retrieving server data.
The template has new electronic forms which have been updated to address the realities of today. They are:
- Pandemic Planning Checklist
- Vendor Partner DR/BC Questionnaire
Areas covered by the template are:
- Business and IT Impact analysis - risk assessment
- Electronic communications - records management and archiving
- HIPAA recovery regulations
- Data backup solutions
- Extended application recovery
- Disaster readiness testing
- Windows client and server recovery
- Crisis management
- Incident Communication Plan and Policy
- Meeting ISO 22301 and 27031 Disaster Planning Requirements
Besides all the great information included in the Disaster Planning e-book, a PDF version of our Disaster Recovery Planning Template and MS WORD version of the template provide a variety of unique, hands-on planning resources to help ensure your organization's disaster readiness as no other product on the market can. So do not delay—order Janco's Disaster Recovery Business Continuity Template today!
2024 Edition of IT Management Tool Kit Released
CIOs and CTOs are in a constantly evolving field, however world class CIOs and CTOs focus on three areas to help them manage more effectively. They are:
- Technology
- People
- Infrastructure
Over 2,500 pages of "Best Practices", tips and techniques, policies, procedures, job descriptions, electronic forms and much more. Ready for immediate download.
Read on Order Management Tool Kit
2024 Edition WFH & Mobility Policy Bundle Updated
Managing the increase of mobile computing enterprises has created a need to have a set of policies and procedures to govern the use of mobile devices. The latest addition of the Mobility Policy bundle has been completely updated to meet the latest security and compliance requirements.
WFH & Mobility Infrastructure Policies and Procedures just updated
- Mobility Policy Bundle - Complies with all mandated, ISO and EU requirements. Provided as individual MS Word and PDF files. The procedures come with 15 full job descriptions and 30 electronic forms which are easily modifiable. Included are:
- BYOD Policy Template
- Mobile Device Access and Use Policy
- Privacy Compliance Policy
- Record Classification, Management, Retention, and Destruction Policy
- Social Networking Policy
- Travel and Off-Site Meeting Policy
- Wearable Device Policy - WYOD
- WFH & Telecommuting Policy
- Chief Mobility Officer job description
Read On Order WFH & Mobility Policy Bundle Download Sample
2024 Security Manual Template Released
Latest version of the Security Manual Template has been released. The right tool to have to better manage threats and information security. New administrator IT Security features include:
- SIEM (Security Information and Event Management) which includes BEST PRACTICES and KPI METRICS
- Audit, governance, and compliance tools
- Chapter on Identity Protection and what enterprises need to do to protect their users.
- eReader (.ePub) version that can be shared on tablets and smartphones
- 25 electronic forms that support mandated compliance requirements.
IT Infrastructure Architecture with 24 months of update service now available 2024 Edition
Janco has just released its IT Infrastructure Architecture with the ability to get updates to all of its components for 24 months from the date of its purchase. Necessary for certification of compliance.
Read On Order IT Infrastructure Architecture Download Sample
10 Backup Best Practices White Paper Released
 Janco has just released a white Paper that defining the 10 Backup Best Practices. It defines how to supplement a disaster recovery and business continuity back-up solution with the cloud. A copy of this key document is available to members of Janco's social network.
Janco has just released a white Paper that defining the 10 Backup Best Practices. It defines how to supplement a disaster recovery and business continuity back-up solution with the cloud. A copy of this key document is available to members of Janco's social network.
To join and get a copy of this white paper register here.