Travel, Electronic Meetings, and Off-Site Meeting Policy
 Protect your data from lost and theft - Now Includes Best Practices for International Travel
Protect your data from lost and theft - Now Includes Best Practices for International Travel
Travel, Electronic Meetings, and Off-Site Meeting Policy - Protection of data and software is often is complicated by the fact that it can be accessed from remote locations. As individuals travel and attend off-site meetings with other employees, contractors, suppliers and customers data and software can be compromised. This policy is eight (8) pages in length and covers:
- Laptop and PDA Security
- BYOD Security
- Wireless and Virtual Private Networks (VPN)
- Data and Application Security
- Public Shared Resources
- Service Provider Selection
- Minimizing attention
- Off-Site Meetings
- Electronic Meetings
- Remote Computing Best Practices
Comes in MS WORD, pdf, and eBook formats - easy to customize
This policy has been updated to reflect the requirements of PCI-DSS, Sarbanes-Oxley, HIPAA, and ISO. The policy comes as both a WORD file and a PDF file utilizing a standard CSS style sheet.
Included are seven (7) electronic forms:
- Mobile Device Access and Use Agreement
- Mobile Device Security Security and Compliance Checklist
- Privacy Policy Compliance Agreement
- Telecommuting IT Checklist
- Telecommuting Work Agreement
- Work From Home IT Checklist
- Work From Home Work Agreement
Also included are five (5) detail job descriptions
- Chief Experience Officer
- Chief Mobility Officer
- Manager Help Desk Support
- Manager Telecommuting
- Manager WFH Support
Order Travel and Off-Site Meeting Policy Download Selected Pages
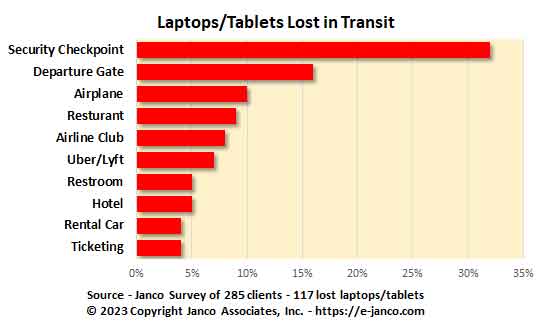
Laptops can and do get lost or stolen. In studies conducted by several security firms, it has been found that over 50% of all lost or stolen laptops disappear at airport security checkpoints an departure gates. Unfortunately almost 70% of these laptops are never recovered.
Order Travel and Off-Site Meeting Policy Download Selected Pages
IT Infrastructure Policies and Procedures
There are other policies that are contained in the IT Infrastructure policies bundle that you should review for applicability. These include:
- Backup and Backup Retention Policy
- Blog and Personal Web Site Policy Includes electronic Blog Compliance Agreement Form
- BYOD Policy Template Includes electronic BYOD Access and Use Agreement Form
- Google Glass Policy Template Includes electronic Google Glass Access and Use Agreement Form
- Internet, e-mail, Social Networking, Mobile Device, Electronic Communications, and Record Retention Policy Includes 5 electronic forms to aid in the quick deployment of this policy
- Mobile Device Access and Use Policy
- Outsourcing and Cloud Based File Sharing Policy
- Privacy Compliance Policy
- Record Classification, Management, Retention, and Destruction policy
- Safety Program
- Text Messaging Sensitive and Confidential Information
- Wearable Device Policy
Read On Infrastructure Policies
NOTE: This policy can be acquired as a standalone item or as part of the CIO IT Infrastructure Policy Bundle or the CIO Management Tool Kit. This product can be acquired with the standard 3 months of update service or with 12 or 24 months with upgrades. The upgrades can be acquired at the time of purchase or with special Janco offers. Individuals who acquire this product via a third party need to contact us directly to order the upgrade service. Individuals who acquire this product via a third party may or may not get the 3 months of update service depending on the the vendor it was acquired from.
